MD5 Hash Generator
Md5 hash generator is commonly used for data encryption. In order to use the tool, write or paste the text you wish to convert below and click on the ‘Generate’ button.
Share on Social Media:

The protection of our data has become essential in the digital age. Protecting sensitive information is moving to the top of the priority list as a result of the increased risks of cyber threats and breaches. Utilizing hash functions that are cryptographic in nature is one of the simplest methods to improve data security.
The MD5 hash is a well-known and commonly used method for data protection among these. This thorough guide will go into the world of MD5 hash generators online, examining their relevance, usefulness, and the larger hash generator ecosystem, which also includes SHA-1, bcrypt, and base64.
Daily Search Query Usage Limit for Our Tool is Explained Below:
| Daily Usage | |
|---|---|
| 👤 - Gust Users: | 10 - 🔎 Search Query |
| 👋 - Registered Users: | 15 - 🔎 Search Query |
| 👦 - Basic Premium Users: | 25 - 🔎 Search Query |
| 👨✈️ - Professional Users: | 35 - 🔎 Search Query |
| 👮♂️ - Agency Users: | 50 - 🔎 Search Query |
| 🏢 - Enterprises / Organizations: | 75 - 🔎 Search Query |
Understanding MD5 Hashing
MD5, which stands for Message Digest Algorithm 5, is a popular cryptographic hash function. Its principal function is to generate a fixed-length hexadecimal hash value from an input (often a text or file). This hash value is unique to the input data and can be used for a variety of applications, such as data integrity checking and password storage.
The Benefits of MD5 Hash Generator Online
The online MD5 hash generator has transformed the way we encrypt our data. Its simplicity comes from its availability via web browsers, which minimizes the need for manual program installation. With a few mouse clicks, you can generate an MD5 hash of your entered data, adding a higher level of security to your sensitive data.
How to Use an Online MD5 Hash Generator?
Using an online MD5 hash generator is really simple:
Input: Enter your text into the above field.
Generate: Click the "Generate" button to begin.
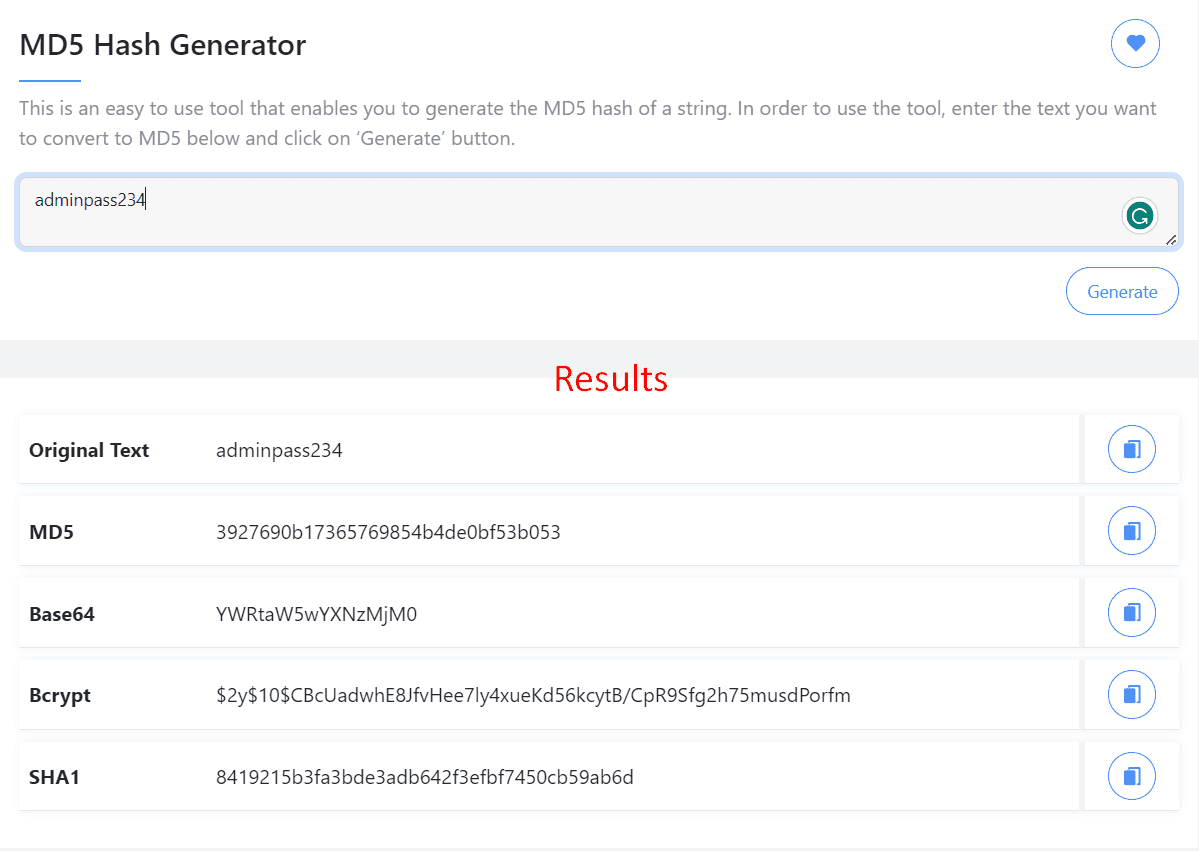
Results: Receive the MD5 hash value associated with your input in real time.
Advantages of MD5 Hashing
- Data Integrity: MD5 hashes act as data fingerprints. Even little changes in the input result in an entirely different hash, making it easy to detect tampering.
- Password Storage: MD5 hashes are used to securely store passwords. Websites save the MD5 hash of the password rather than the real password. Even if the database is compromised, the attackers will not have quick access to user passwords.
- Quick Verification: MD5 hashes make it easier to check the authenticity of the information. To confirm that a downloaded file hasn't been modified during transit, verify its hash with the defined hash value.
Limitations of MD5 Hashing
While MD5 hashes offer numerous benefits, they also have limitations, primarily related to their vulnerability to certain attacks. Over time, researchers have demonstrated collision vulnerabilities, where two different inputs produce the same hash. This weakness has led to the decreased use of MD5 in critical security applications.
Seo Top Tools generate hashes such as SHA-1, bcrypt, and Base64.
- SHA-1 Hash Generator: Another extensively used hashing algorithm is Secure Hash Algorithm 1 (SHA-1). It generates longer hash values than MD5 and is said to be more secure. Online SHA-1 hash generators function similarly to MD5 generators, giving better data security.
- Bcrypt Hash Generator: Bcrypt was created primarily for securely hashing passwords. It includes a "work factor" that may be changed to make brute-force attacks more time-consuming and resource-intensive. Online bcrypt hash generators offer a strong password security option.
- Base64 Hash Generator: Unlike cryptographic hashes, Base64 encoding isn't designed for security but for data representation. It converts binary data into ASCII text, making it suitable for scenarios like encoding images in URLs. While it's not a hash function, understanding its purpose adds to your knowledge of data manipulation.
FAQ's
What is an MD5 hash generator online?
An online MD5 hash generator accepts an input (such as text or a file) and generates a unique MD5 hash result. This hash serves as a digital fingerprint of the input data, enabling confidentiality and password security verification.
What exactly does an MD5 hash generator do?
An MD5 hash generator applies the MD5 hashing algorithm to the data. The algorithm analyzes the input data and generates a fixed-length decimal hashing value no matter its size. Even minor changes in the input cause a significant difference in the hash value.
What is the operation of an MD5 hash generator?
The MD5 hashing technique is applied to the input by an MD5 hash generator. Regardless of the volume of the input, the algorithm evaluates it and creates a fixed-length hexadecimal hash result. Even slight changes in the input result in a huge variance in the hash value.
What are the benefits of utilizing an online MD5 hash generator?
Using an online MD5 hash generator offers various benefits, including rapid data integrity checks, safe password storage, and simplicity of usage. It helps creating MD5 hashes easier without requiring application installation.
Is MD5 hashing still safe to use?
Because of its vulnerability to collision attacks, MD5 hashing is no longer considered safe for essential security applications. However, it is still helpful for non-critical applications such as checksum checking and basic data protection.
Are online MD5 hash generators secure to use?
Reputable and reputable online MD5 hash generators are typically safe to utilize for non-critical applications. However, take caution and verify you're utilizing a reputable tool to prevent any security hazards.
Can I use MD5 hashes for password storage?
While MD5 hashes were traditionally used for password storage, they are not recommended owing to their weaknesses. For safe password storage, it's advised to utilize bcrypt or other current password hashing algorithms.
What are some alternatives to MD5 hashing?
Alternatives to MD5 hashing include SHA-1, which provides longer and more secure hashes, bcrypt, particularly developed for password hashing, and Base64 encoding, which is used for data representation rather than security.
What is the typical length of an MD5 hash value?
MD5 can generate a 128-bit (16-byte) hash value and has a hexadecimal number of 32 digits.
Is it permissible for me to decrypt MD5?
No. Because MD5 is not an encryption algorithm, it can't be decrypted. Many people are puzzled by this since they believe MD5 can encrypt data. In reality, MD5 does not provide encryption. It can only compute the hash value for a certain collection of data.
Is it possible to reverse MD5?
The answer is, once again, no. Because hash functions only work on one-way operations, you aren't allowed to reverse MD5. Only data or messages will be received, digested, and hashed by the MD5 generator. MD5 does not have a reverse function.
Why isn't MD5 reversible?
Consider the following example to see why MD5 is not reversible: if we use the MD5 online generator on 360,000 characters of text, we will get a digest of roughly 32 digits. So, how could the algorithm calculate the accuracy with which 750,000 characters were used from only 32 digits if we wished to reverse this? This is why the MD5 generator does not have a function like this.